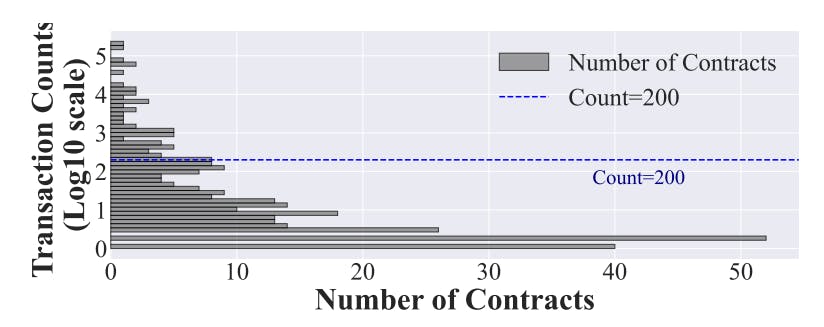
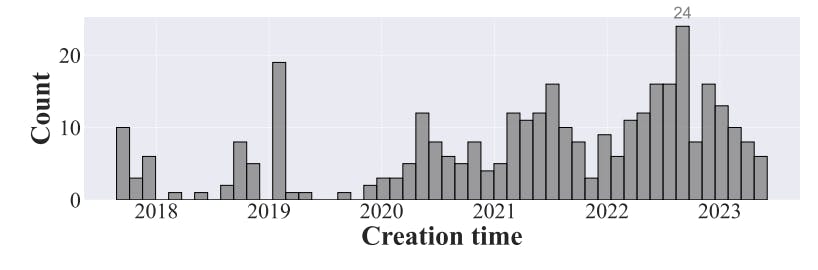
#smart-contracts
#smart-contracts
[ follow ]
#blockchain #ethereum #vulnerability-detection #defi #security #avverifier #transaction-prioritization
Real estate
fromLondon Business News | Londonlovesbusiness.com
1 month agoTop 10 real estate tokenisation development companies in 2026 - London Business News | Londonlovesbusiness.com
Real estate tokenisation converts property rights into blockchain tokens enabling fractional ownership, greater capital efficiency, and faster, cheaper transactions.
fromTheregister
2 months agoAn AI for an AI: Anthropic says AI agents require AI defense
The AI upstart didn't use the attack it found, which would have been an illegal act that would also undermine the company's we-try-harder image. Anthropic can probably also do without $4.6 million, a sum that would vanish as a rounding error amid the billions it's spending. But it could have done so, as described by the company's security scholars. And that's intended to be a warning to anyone who remains blasé about the security implications of increasingly capable AI models.
Artificial intelligence
from24/7 Wall St.
2 months agoXRPL Smart Contracts Go Live on AlphaNet: Can DeFi Finally Rescue XRP's Price?
XRP ( ) enters 2026 with years of infrastructure momentum behind it, but its price keeps stalling. Ripple has built payment corridors, secured regulatory clarity, and attracted institutional partners. Yet none of that translated into sustained on-chain activity or consistent price growth. XRP's smart contracts went live on AlphaNet on November 7, 2025, giving developers native Layer-1 capabilities for the first time. The XRP Ledger (XRPL) can now host DeFi applications-lending pools, liquidity protocols, and automated markets-that lock XRP into smart contracts instead of just moving it instantly between wallets.
Cryptocurrency
[ Load more ]