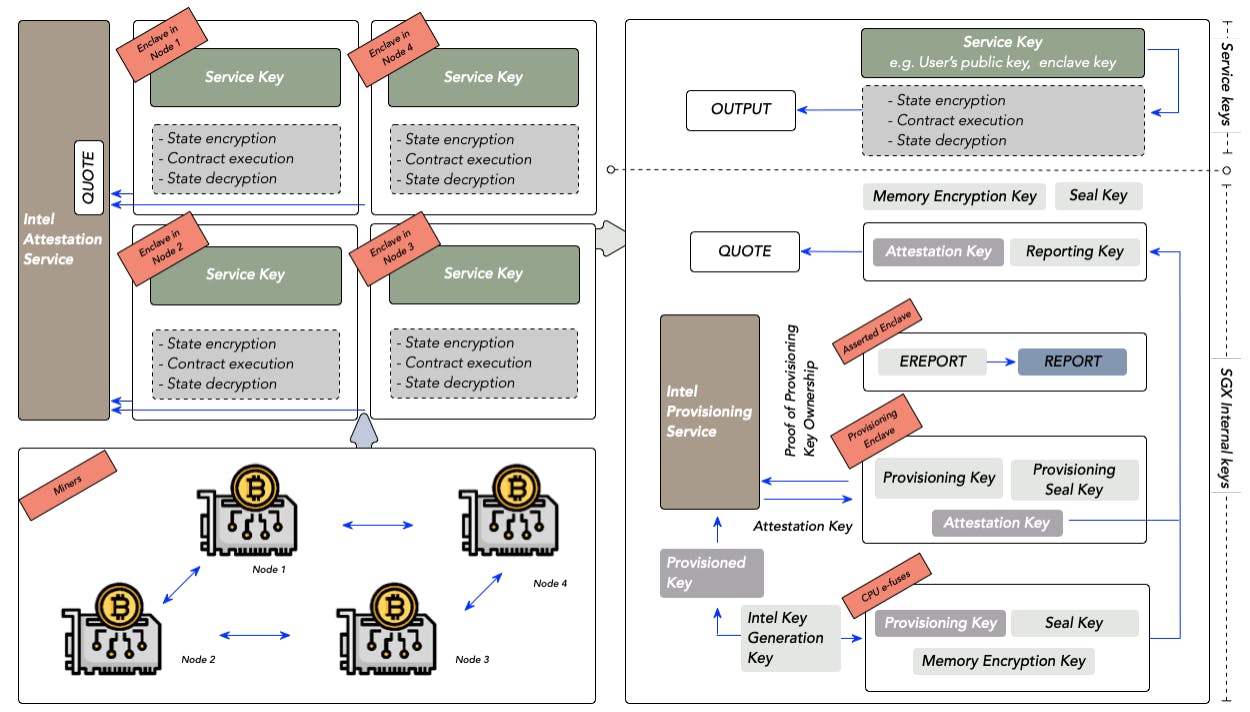
"The TCSC-based voting protocol utilizes Intel SGX to ensure privacy and confidentiality in voting through defined boundaries for trusted and untrusted operations."
"The deployment stage compiles contract codes into enclave codes, incorporating security definitions through Enclave Definition Language (EDL) for managing secret and public states."
The TCSC-based voting protocol leverages Intel SGX to enhance privacy and security in electronic voting systems. It consists of two key stages: the deployment stage and execution stage. During deployment, contract codes are compiled into enclave codes, with critical definitions set for trusted and untrusted components through Enclave Definition Language (EDL). This process defines the boundaries for secret and public states and outlines how to access them. Access Control Functions ensure confidentiality in vote counting until the voting process concludes, protecting sensitive information throughout the election cycle.
Read at Hackernoon
Unable to calculate read time
Collection
[
|
...
]