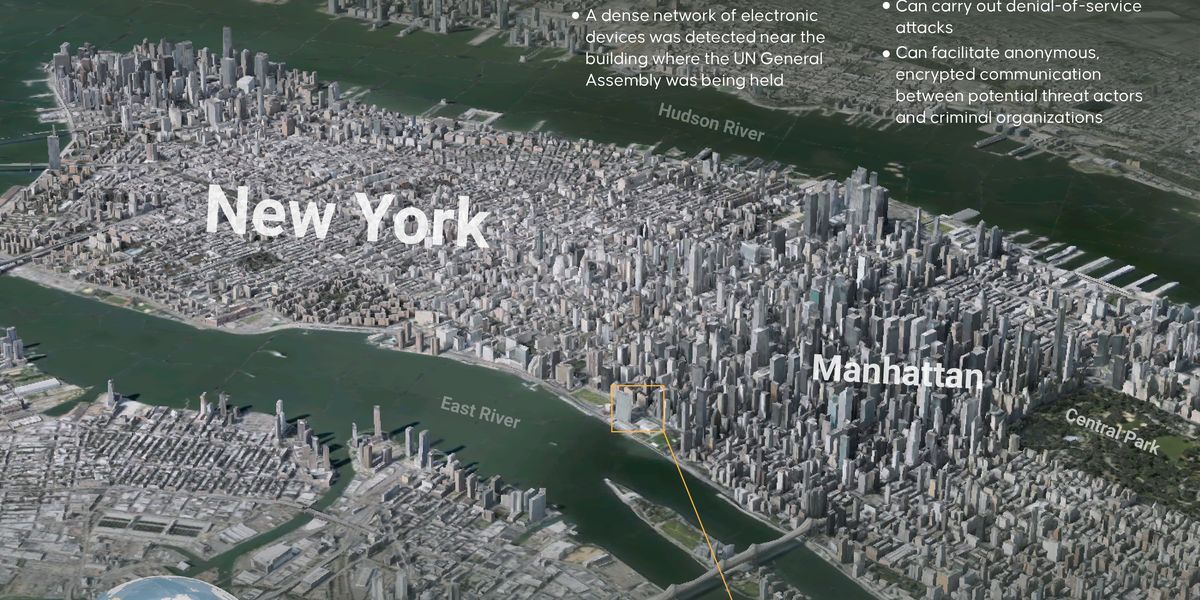
"The devices were designed to what experts call a "SIM farm," an industrial-scale operation where hundreds or thousands of SIM cards can be manipulated simultaneously. These setups are typically associated with financial fraud or bulk messaging scams. Still, the Secret Service warned that they can also be used to flood telecom networks, disable cell towers, and obscure the origin of communications. In the shadow of the UN, where global leaders convene and security tensions are high, the proximity of such a system raised immediate questions about intent, attribution, and preparedness. "(SIM farms) could jam cell and text services, block emergency calls, target first responders with fake messages, spread disinformation, or steal login codes," Jake Braun, Executive Director of the Cyber Policy Initiative at the University of Chicago and former White House Acting Principal Deputy National Cyber Director, tells The Cipher Brief. "In short, they could cripple communications just when they're needed most.""
"At their core, SIM farms exploit the fundamental architecture of mobile networks. Each SIM card represents a unique identity on the global communications grid. By cycling through SIMs at high speed, operators can generate massive volumes of calls, texts, or data requests that overwhelm cellular infrastructure. Such floods can mimic the effects of a distributed denial-of-service (DDoS) attack, except the assault comes through legitimate carrier channels rather than obvious malicious traffic."
""SIM farms are essentially racks of modems that cycle through thousands of SIM cards," Dave Chronister, CEO of Parameter Security, tells The Cipher Brief. "Operators constantly swap SIM cards and device identifiers so traffic appears spread out rather than coming from a single source." That makes them extremely difficult to detect."
Devices were designed to create SIM farms—industrial-scale operations manipulating hundreds or thousands of SIM cards simultaneously. These systems commonly enable financial fraud and bulk messaging scams but also present broader threats: flooding telecom networks, disabling cell towers, and obscuring communication origins. Near high-security events, such setups raise urgent concerns about intent, attribution, and readiness. SIM farms operate by cycling SIMs to generate massive call, text, or data volumes that can overwhelm infrastructure and mimic DDoS effects while using legitimate carrier channels. Operators swap SIMs and device identifiers to spread traffic and evade detection, complicating response and mitigation.
Read at The Cipher Brief
Unable to calculate read time
Collection
[
|
...
]