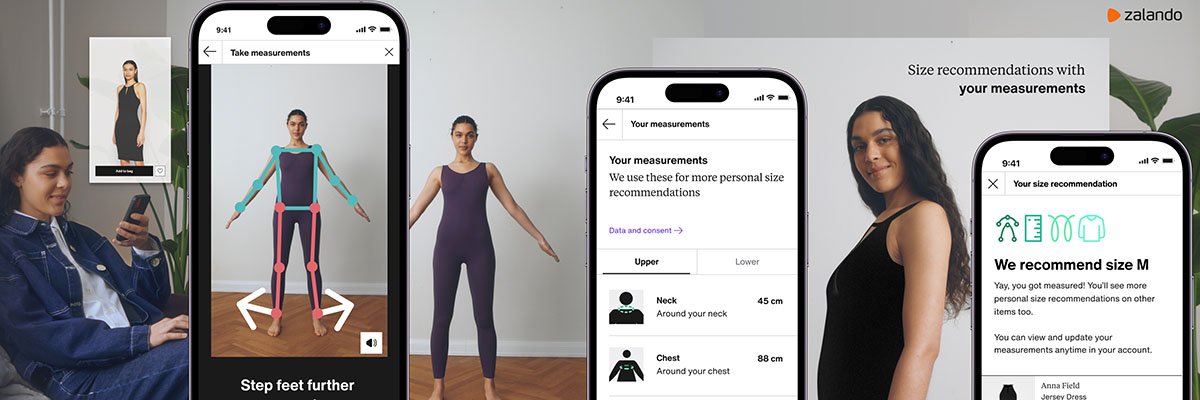
"Today, she is the group chief information security officer (CISO) at Zalando, a high-tech online fashion retailer that boasts over 50 million customers in 26 markets. Zalando, she says, is more of a technology company than a retailer, offering its shoppers artificial intelligence (AI)-powered apps that can help them choose the right outfit for an occasion or take their measurements by capturing an image on a mobile phone."
""I was employee number seven." Security Innovation, as the company became known, developed proof-of-concept exploits to show how security vulnerabilities in software could be misused by hackers or bad actors if they were left unfixed. It was a steep learning curve, says Mottay in an interview with Computer Weekly at a SANS cyber leaders summit in London. "For six months, I used to go home after work and study until 3am on how to create exploits, and I became pretty good.""
"Mottay says she "fell into" a career in computer security after receiving an offer from a university in Florida, where she was studying maths during an exchange programme. "I met a professor of software engineering who must have seen some potential because he said he would sponsor the rest of my bachelor's degree and my master's degree if I agreed to switch from mathematics to software engineering and to work on some of the research grants he was getting," she says."
Florence Mottay began her career in cyber security researching exploits for vulnerabilities at a small US startup. She is the group chief information security officer (CISO) at Zalando, a high-tech online fashion retailer with over 50 million customers across 26 markets. Zalando operates as a technology company, offering AI-powered apps that assist with outfit selection and body measurements from mobile images. Adoption of generative AI created unique security and operational challenges for Mottay and her roughly 100-strong IT team, requiring bespoke approaches because no established blueprints existed. Mottay entered security after switching from mathematics to software engineering with university sponsorship and developed exploit-creation skills through intensive early work at Security Innovation.
Read at ComputerWeekly.com
Unable to calculate read time
Collection
[
|
...
]