"In my previous article Build a Secure DevSecOps CI/CD Pipeline with Jenkins, ArgoCD, Trivy, and Vault I demonstrated building a production-ready pipeline that embedded security and GitOps principles from the ground up. But DevOps isn't static. Threats evolve, tools mature, and teams need pipelines that scale with them. The real challenge isn't just building a pipeline once it's continuously improving it based on production experience and evolving requirements."
"Prerequisites If you followed Part 1, most of the setup is already in place. For this part, you'll specifically need: Technical A Kubernetes cluster with kubectl access A GitHub repository with Actions enabled and admin permissions Knowledge GitHub Actions basics (workflows, secrets, environments) Canary deployment concepts (progressive delivery) Kubernetes Ingress Controller (NGINX) If you're starting fresh, check out the full prerequisites list in [Part 1]."
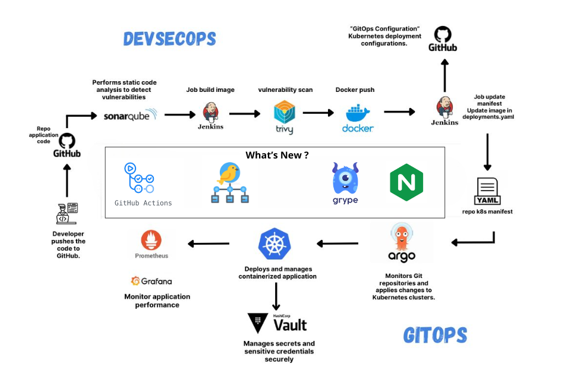
"Quick Recap of Part 1 We built a strong foundation with: Core Architecture: Jenkins CI/CD, ArgoCD GitOps, Trivy scanning, Vault for secrets Security-first approach: Multi-stage scanning, zero-trust secrets, policy-as-code GitOps Workflow: Code Push Jenkins Build Security Scans ArgoCD Sync K8s Deploy Monitoring This pipeline supported multiple applications across teams in development and early production. That recap makes it easier for new readers to catch up, and reminds returning readers of the journey so far before diving into the next stage."
An existing pipeline used Jenkins CI, ArgoCD GitOps, Trivy scanning, and Vault for secrets with a security-first approach featuring multi-stage scanning, zero-trust secrets, and policy-as-code. The workflow moved code through CI builds, security scans, ArgoCD syncs, Kubernetes deployments, and monitoring, supporting multiple applications across teams. Planned improvements include migrating continuous integration to GitHub Actions to reduce Jenkins operational overhead, strengthening secrets and security management, adopting progressive canary deployments for safer rollouts, and exposing applications via an NGINX Ingress Controller. Required prerequisites include Kubernetes access, a GitHub repository with Actions enabled, and familiarity with GitHub Actions and canary concepts.
Read at faun.pub
Unable to calculate read time
Collection
[
|
...
]