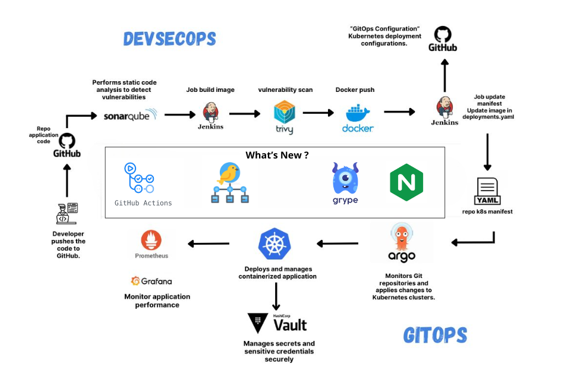
#secrets-management
#secrets-management
[ follow ]
#github-actions #canary-deployments #devsecops #gitops #application-security #cybersecurity #devops #security
fromThe Hacker News
1 month agoThe Future of Cybersecurity Includes Non-Human Employees
As organizations scale Artificial Intelligence (AI) and cloud automation, there is exponential growth in Non-Human Identities (NHIs), including bots, AI agents, service accounts and automation scripts. In fact, 51% of respondents in ConductorOne's 2025 Future of Identity Security Report said the security of NHIs is now just as important as that of human accounts. Yet, despite their presence in modern organizations, NHIs often operate outside the scope of traditional Identity and Access Management (IAM) systems.
Information security
fromThe Hacker News
4 months agoProduct Walkthrough: How Passwork 7 Addresses Complexity of Enterprise Security
Passwork is positioned as an on-premises unified platform for both password and secrets management, aiming to address the increasing complexity of credential storage and sharing in modern organizations. The platform recently received a major update that reworks all the core mechanics. Passwork 7 introduces significant changes to how credentials are organized, accessed, and managed, reflecting feedback from real-world users. The redesign prioritizes usability and security, with a focus on streamlining workflows and making key features more accessible.
Information security
Information security
fromHackernoon
2 years agoFrom Repos to Risks: How Hardcoded Secrets in GitHub Source Code Create Security Risks | HackerNoon
Hardcoded secrets in source code expose organizations to significant security risks, necessitating greater awareness and secure practices in development environments.
[ Load more ]