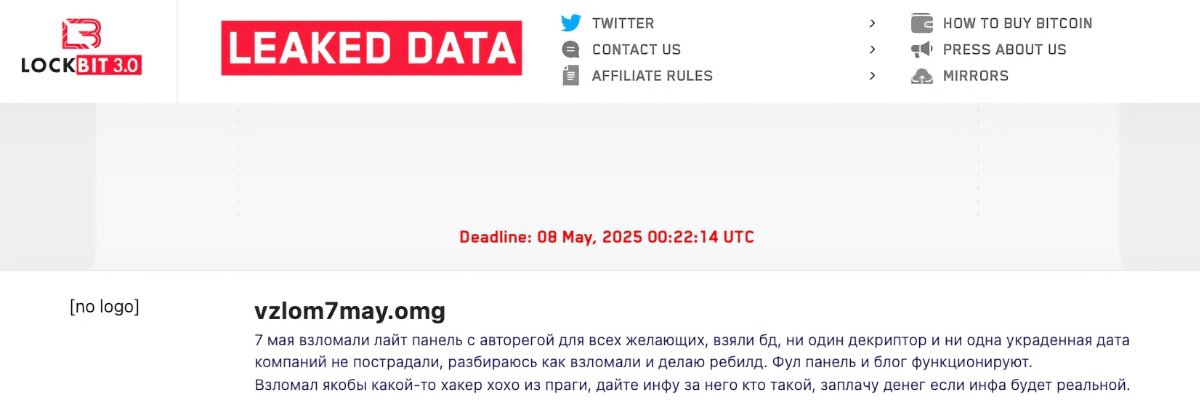
"The entire contents of the SQL database of a web administration interface for LockBit's affiliates was made public, revealing critical information about ransomware operations."
"Data revealed a striking gap of up to 10 days between the end of data exfiltration and the launch of encryption, underscoring the need for better detection."
"The LockBit administration interface had 75 user accounts, with 44 involved in generating ransomware attacks, shedding light on the group's operational structure."
"The analysis shows that 35.5% of LockBit's ransomware activities targeted victims in the Asia-Pacific region, highlighting a shift in crime geography."
On 7 May 2024, the UK National Crime Agency exposed the identity of LockBit 3.0 operator Dmitry Khoroshev. A year later, critical data from an SQL database of the ransomware's affiliate operations was leaked. This unprecedented data provides insight into LockBit's attack patterns, allowing for better estimates of attack dates and victim attribution. Despite a focus on Asian targets, the operational structure has revealed that many affiliates have paused their accounts or were inactive, raising questions about the stability of the ransomware organization and the effectiveness of ongoing combat efforts.
Read at ComputerWeekly.com
Unable to calculate read time
Collection
[
|
...
]