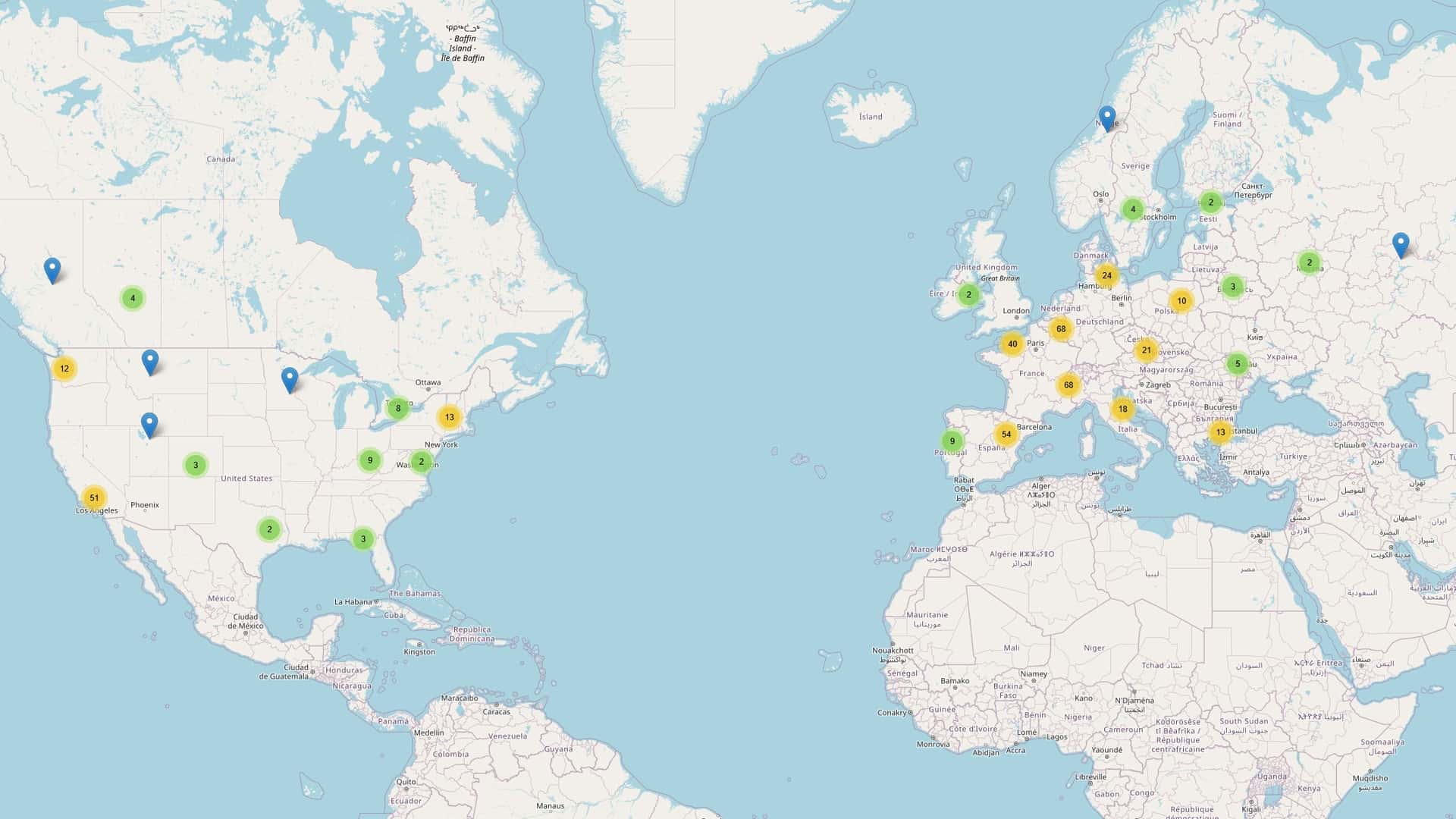
"Over 1,300 publicly accessible TeslaMate dashboards were discovered by Seyfullah Kiliç, founder of cybersecurity company SwordSec, by scanning the internet with simple tools to expose instances that were not secured, either with a password or behind a firewall or a virtual private network VPN). TeslaMate is an open-source data logger and visualizer for Tesla electric vehicles, which allows owners to run a server and keep tabs on charging sessions, temperatures, battery health, driving speed, location history and much more."
"As reported by TechCrunch, Kiliç wrote in a blog post that he was able to access everything on the discovered TeslaMate instances, including the location of the vehicles, which allowed him to build a map of cars that are running potentially compromised TeslaMate installations. And because the servers were not protected in any way, he could also change settings for data collection, just like the owner would."
""For everyday Tesla owners deploying TeslaMate, this is dangerous," the researcher wrote. "You're unintentionally sharing your car's movements, charging habits, and even vacation times with the entire world." So, what can be done to limit this sort of leak? The TeslaMate server must be secured, according to Seyfullah Kiliç, either by enabling basic username and password authentication, limiting access to trusted IP addresses, or binding the service to the local host and exposing it only through a VPN."
Over 1,300 TeslaMate dashboards were publicly accessible without authentication, exposing vehicle location histories and detailed telemetry. Unprotected instances allowed full access to logs and the ability to alter data collection and settings remotely. TeslaMate is an open-source data logger and visualizer that records charging sessions, temperatures, battery health, driving speed, and location history when self-hosted. Publicly hosting the service without protections creates significant privacy and safety risks, including mapping vehicle movements and revealing routines. Recommended mitigations include enabling basic username/password authentication, restricting access to trusted IPs, binding the service to localhost, or exposing it only through a VPN.
Read at InsideEVs
Unable to calculate read time
Collection
[
|
...
]