"LinkedIn has redesigned its static application security testing pipeline (SAST) to provide consistent, enforceable code scanning across a GitHub-based, multi-repository development environment. The initiative was a result of the company's shift-left strategy by delivering fast, reliable, and actionable security feedback directly in pull requests, strengthening the security of LinkedIn's code and infrastructure and helping protect members and customers."
"At a high level, SAST analyzes source code to identify potential vulnerabilities early in the development lifecycle. At LinkedIn's scale, legacy approaches that relied on multiple disconnected scanners and custom integrations resulted in uneven coverage, limited visibility into pipeline health, and friction for developers. The redesign aimed to standardize scanning, simplify adoption, and more deeply embed security into developer workflows without introducing bottlenecks."
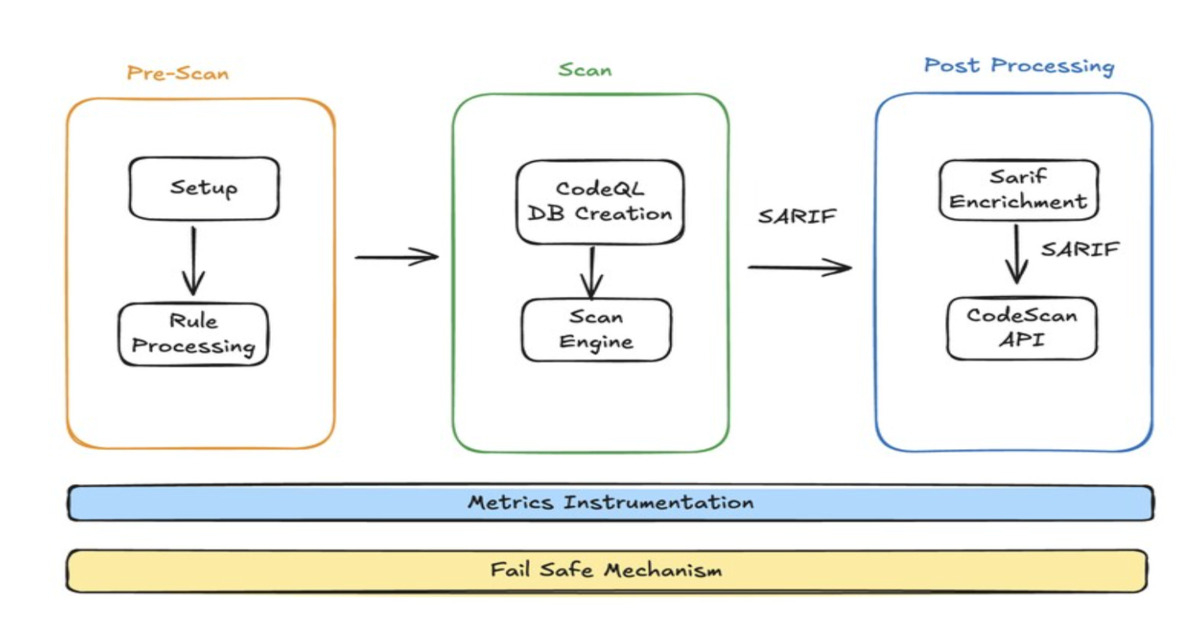
"The new architecture leverages GitHub Actions to orchestrate two primary scanning engines, CodeQL and Semgrep, chosen for their complementary coverage and extensibility. LinkedIn engineers implemented custom workflows to manage rule execution, orchestrate scanning, and process results. Findings are normalized using the SARIF standard and enriched with metadata to provide clear remediation guidance and actionable context for both developers and security teams."
LinkedIn redesigned its static application security testing (SAST) pipeline to deliver consistent, enforceable code scanning across a GitHub-based, multi-repository environment. The redesign prioritized fast, reliable, and actionable security feedback directly in pull requests to strengthen code and infrastructure security for members and customers. Engineers established guiding principles: developer-first security to minimize workflow interruptions, extensibility for additional rules and integrations, resilience to prevent developer-impacting failures, and observability for coverage and performance monitoring. The new architecture uses GitHub Actions to orchestrate CodeQL and Semgrep, with custom workflows to execute rules and process results. Findings are normalized to SARIF and enriched with metadata for clear remediation guidance.
Read at InfoQ
Unable to calculate read time
Collection
[
|
...
]