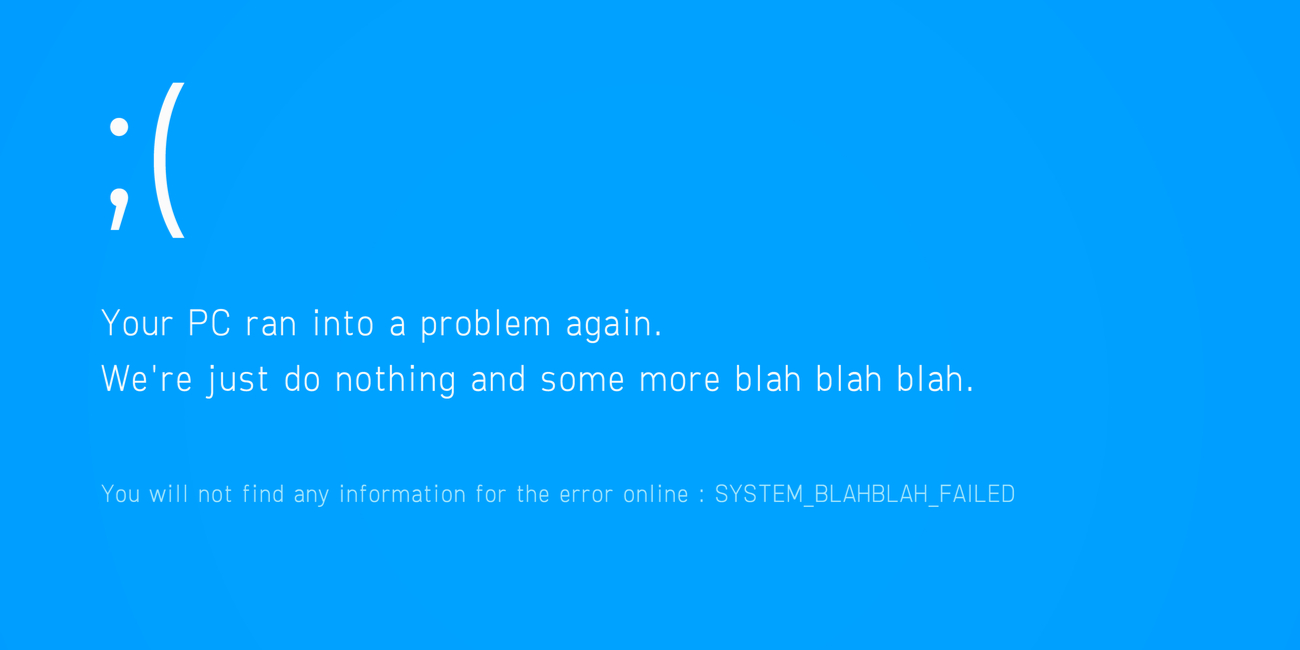
"The setup is straightforward: a hotel worker receives an email that appears to be from Booking.com, usually warning about an eye-watering charge in euros. When they follow the "See details" link, they're taken to what looks like a real Booking.com page - except instead of a reservation, they're met with a fake verification screen that quickly gives way to a full-screen Windows BSOD scare."
"The bogus BSOD is designed to panic the user into "fixing" the non-existent error by performing a series of steps that ultimately have them paste and execute a malicious PowerShell command, the classic hallmark of a ClickFix attack. Because the victim manually runs the code themselves, it sidesteps many automated security controls that would block traditional drive-by malware download methods."
Russia-linked attackers target European hotels and hospitality outlets using Booking.com-themed phishing that leads victims to fake verification pages and a full-screen Windows Blue Screen of Death (BSOD) scare. The campaign, called PHALT#BLYX, employs a social engineering ClickFix variant that panics staff into pasting and executing a malicious PowerShell command. Because victims run the code manually, the attack bypasses many automated security controls. The executed command downloads additional files and leverages legitimate Windows components to run attacker code, ultimately installing a remote access trojan that provides persistent access and enables further malware delivery. The attackers shifted from HTML Application to MSBuild-based execution.
Read at Theregister
Unable to calculate read time
Collection
[
|
...
]