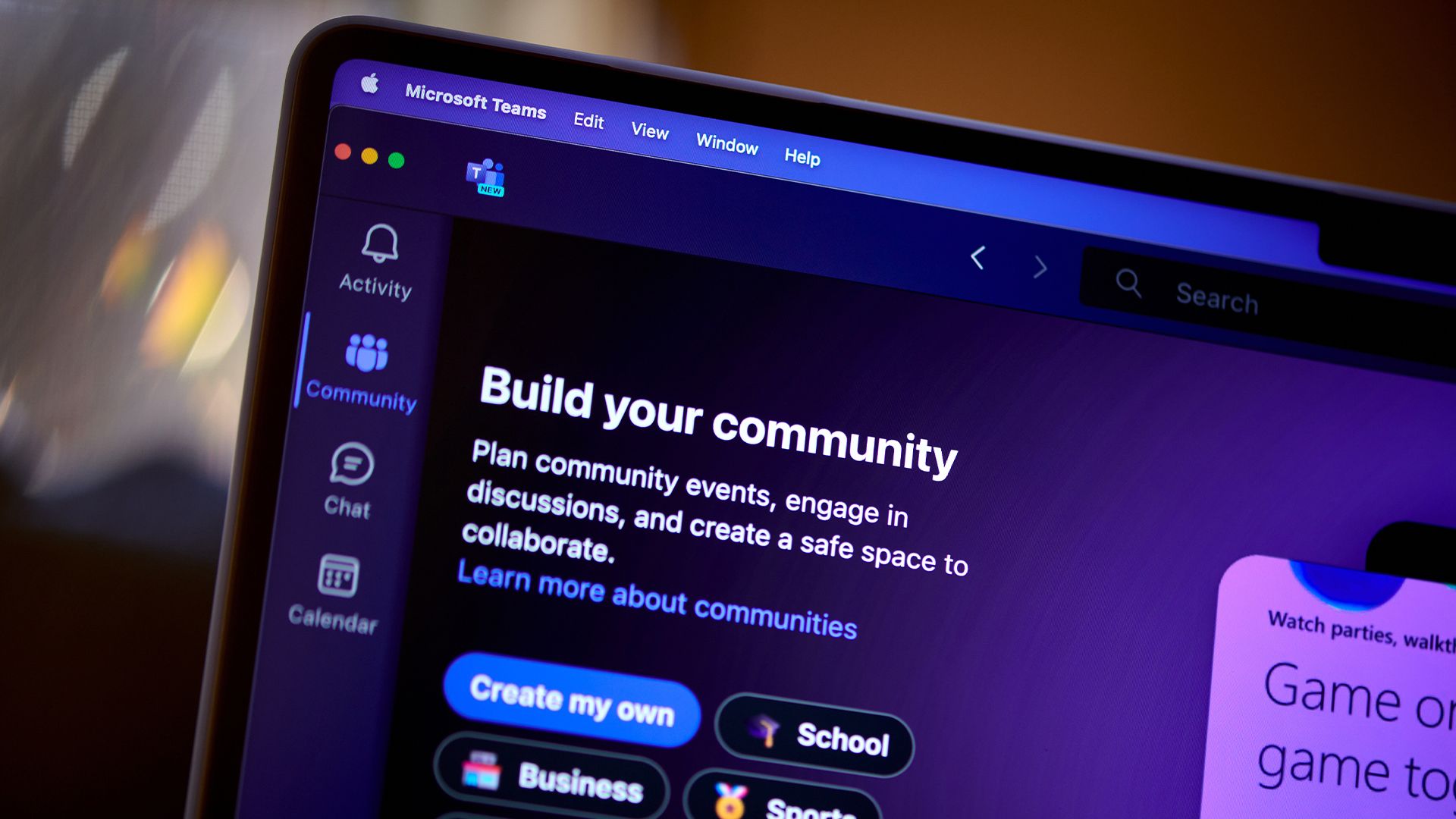
"The current infection chain is built on a highly successful malvertising model. Threat actors buy Bing search engine advertisements to direct users to convincing-looking, but malicious landing pages," said Aaron Walton, threat intelligence analyst at Expel. "These search engine ads put links to the download right in front of potential victims. The most recent campaigns push ads for Microsoft Teams and impersonate the download pages. However, they've also cycled through other popular software such as PuTTy and Zoom."
""The certificates they use regularly get revoked by the certificate's issuer, so new instances of the malware with a valid certificate indicate a new run of the campaign," he said. "On any given day the bad actors may use multiple certificates, but seeing their files with a new fresh certificate also helps us know they're still active. These new certificates further indicate steady investment into their campaign."
Malicious actors are running malvertising campaigns that buy Bing search ads to direct users to convincing but malicious landing pages that impersonate software downloads, including Microsoft Teams, PuTTy, and Zoom. These campaigns deliver OysterLoader (formerly Broomstick and CleanUpLoader), an initial-access tool that installs a backdoor to maintain persistent access to infected devices and networks. The malware is packed to hide capabilities and maintain a low static detection rate. Threat actors also use code-signing certificates to increase trust in malicious files; frequent certificate revocations and new certificates indicate repeated campaign runs and sustained investment.
Read at IT Pro
Unable to calculate read time
Collection
[
|
...
]