"When suspicious activity is detected, the system can automatically terminate the associated user sessions, reducing the security detection and response gap from potential days or hours to minutes. Slack engineers Nathan Lehotsky and Ryan Persaud emphasized the company's approach to security: Trust is our number one core value. We believe security is a shared responsibility between us and our customers by empowering them with data and tools to build security solutions while also fostering a secure platform and neutralizing threats."
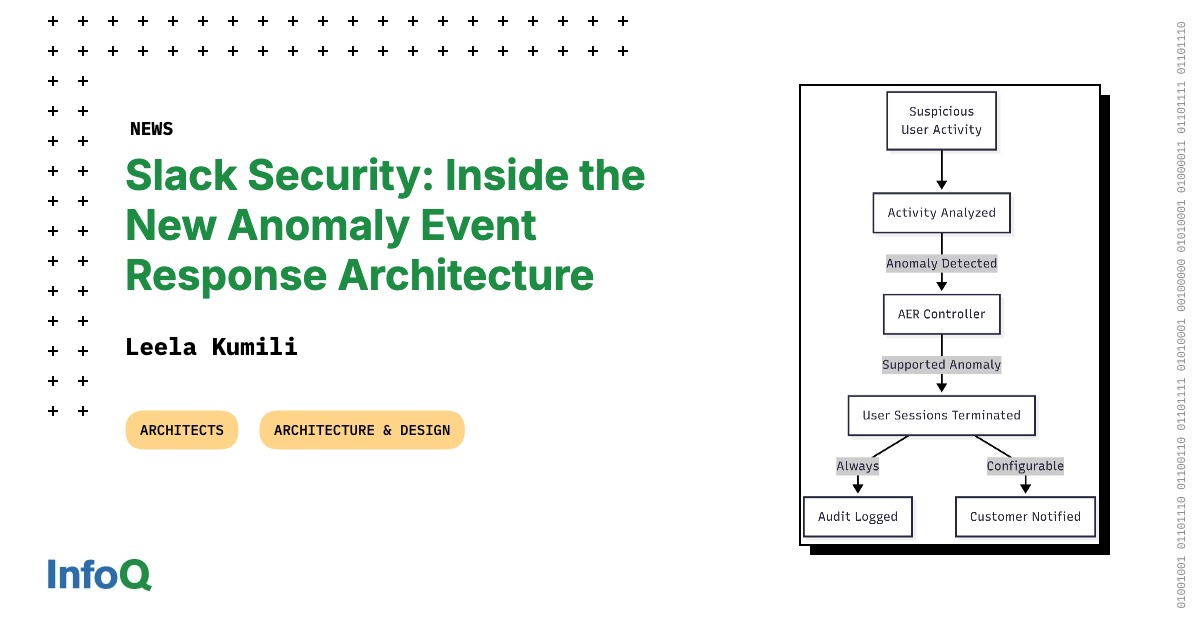
"The architecture of Anomaly Event Response consists of three main components: a detection engine, a decision framework, and a response orchestrator. The detection engine continuously monitors billions of Slack events daily, applying rule-based heuristics and dynamic thresholds tailored to each organization's usage patterns. It identifies unusual activities such as logins from Tor exit nodes, rapid file downloads, excessive API calls, session fingerprint mismatches, and non-standard user agents."
Anomaly Event Response (AER) autonomously detects high-confidence threat behaviors across Slack by continuously monitoring billions of events and applying rule-based heuristics and dynamic, organization-specific thresholds. The detection engine flags signals such as logins from Tor exit nodes, rapid file downloads, excessive API calls, session fingerprint mismatches, and non-standard user agents. The decision framework validates anomalies against internal rules and tenant configuration to reduce false positives. The response orchestrator executes predefined actions including terminating affected sessions, generating audit logs, and notifying relevant security teams. Automated responses shorten the detection-to-mitigation window from days or hours to minutes while routing alerts appropriately.
Read at InfoQ
Unable to calculate read time
Collection
[
|
...
]