"In the below article, we mastered the fundamentals of Linux permissions: rwx, chmod, chown, and chgrp. We learned how to read and change permissions for the User, Group, and Other. Along with the permissions mentioned in the above article, there are special permissions. They are not about just reading or writing; they are advanced flags that change the behavior of executables and directories. These permission bits enable: Program execution with elevated privileges (securely) Collaborative directory access in shared environments Controlled delete permissions in public directories"
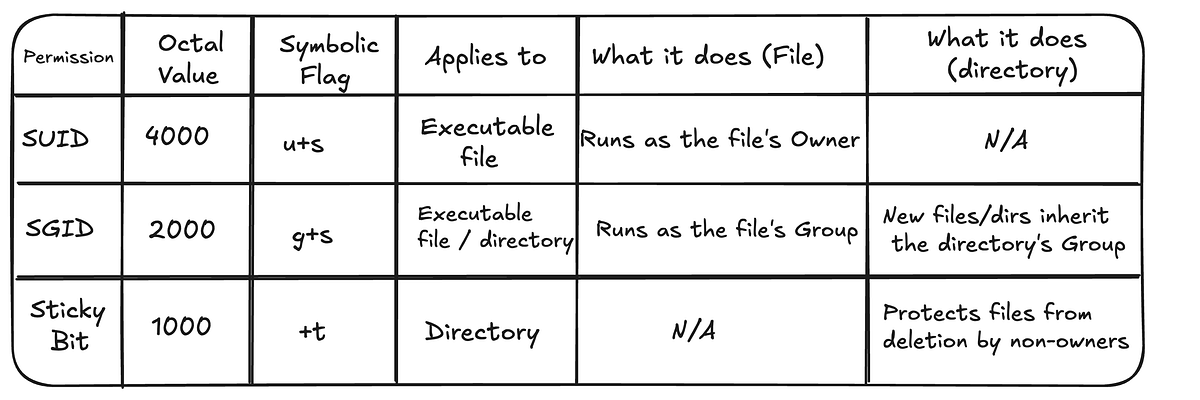
"Let's do a deep dive, with examples. 1. The SUID (Set User ID) Bit: "Run as the Owner" The SUID bit applies only to executable files. What it is: A flag that tells Linux to execute this program with the permissions of the file's owner, not the user who is running it. How to Read It: You'll see an s in the user's execute (x) position. rwsr-xr-x: The SUID bit"
SUID causes an executable to run with the file owner's privileges rather than the invoking user's, and appears as an 's' in the user execute position. SGID on executables makes them run with the file's group; on directories it forces new files to inherit the directory group, enabling collaborative workflows. The sticky bit on directories prevents users from deleting or renaming files they do not own, useful for shared temporary spaces. Use chmod u+s, g+s, and +t or octal prefixes (setuid=4, setgid=2, sticky=1) to set these bits. Exercise caution with SUID programs, especially when owned by root.
Read at Medium
Unable to calculate read time
Collection
[
|
...
]