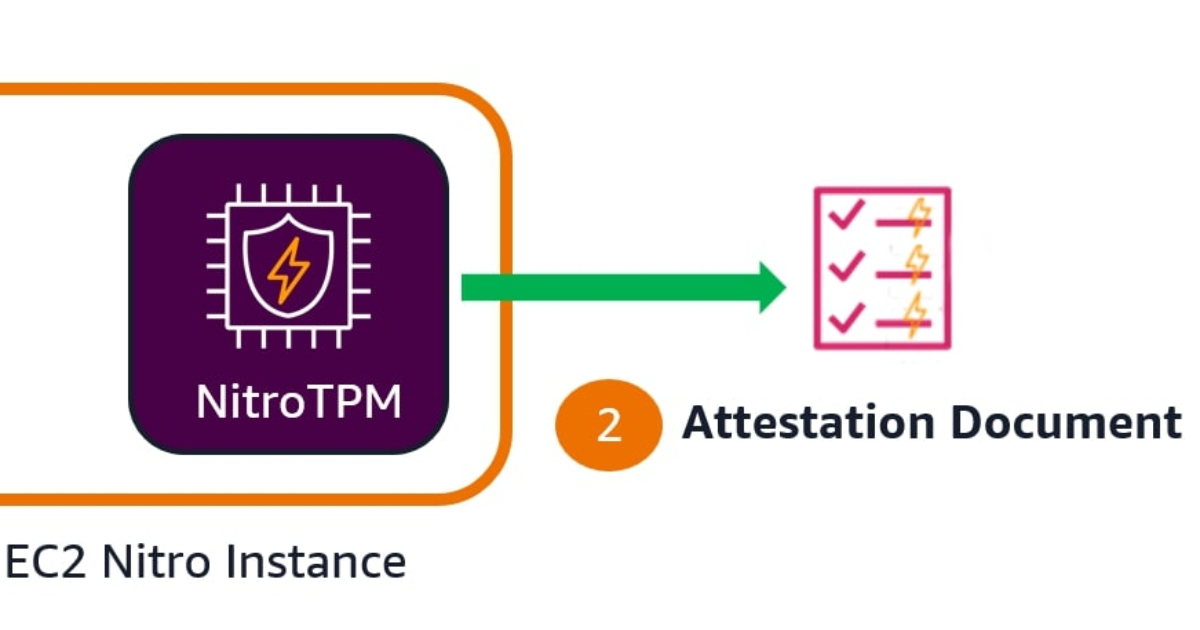
"AWS has introduced EC2 instance attestation, a new security feature that enables customers to verify that their virtual machines are running approved software configurations in a cryptographically secure manner. The capability is powered by the Nitro Trusted Platform Module ( NitroTPM) and Attestable AMIs. With EC2 instance attestation, customers can cryptographically verify that an EC2 instance is running trusted configurations and software, addressing a key concern for organizations with strict security and compliance requirements."
"Similar to the functionality previously available only in Nitro Enclaves, the new feature extends those protections to standard EC2 instances. Bean adds: "This release provides tooling and interfaces for customers to build hardened and constrained Amazon Machine Images (AMI), which are designed for zero operator access and high assurance. These attestable AMIs can provide proof to external systems of the system contents to inform authentication and authorization decisions.""
EC2 instance attestation enables cryptographic verification that virtual machines run approved, trusted software configurations using the Nitro Trusted Platform Module (NitroTPM) and Attestable AMIs. Organizations can verify that instances run hardened, constrained AMIs designed for zero operator access and high assurance. Attestable AMIs include a cryptographic hash of all contents, covering applications, code, and the boot process. The feature extends protections formerly limited to Nitro Enclaves to standard Nitro-based EC2 instances, preserving high-performance networking and AI accelerator support. AWS Key Management Service can restrict decryption of keys and secrets so only instances running an approved AMI can access them.
Read at InfoQ
Unable to calculate read time
Collection
[
|
...
]